Keystone is the key component for OpenStack Authentication. Every requests via API must be checked and
verified by Keystone. In general , when the clients provide a valid
username/password combination, the OpenStack keystone will provide a token, the
following comminucation will be based on the token. There are two ways of
authentication for keystone due to the way how client provides their
identification: UUID and PKI.
Universally Unique IDentifier (UUID)
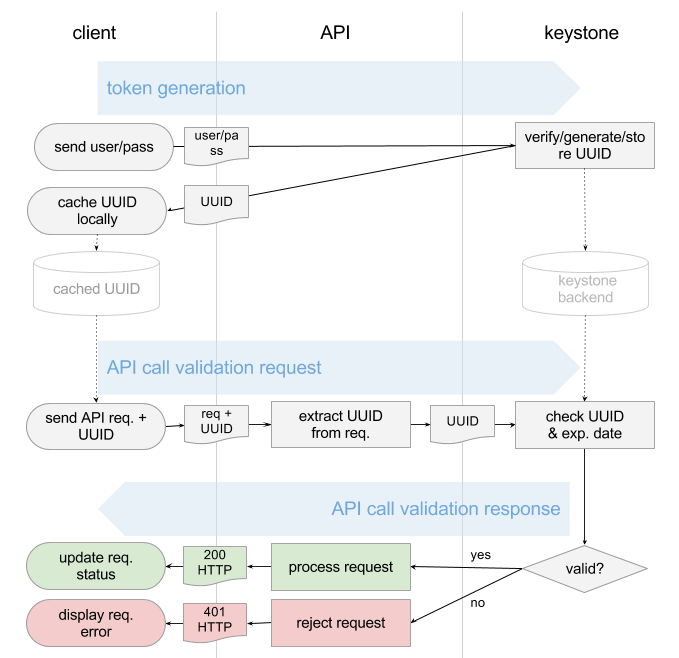
1. Client send the username/password to keystone
2. Keystone service verify the username/password pair
3. Keystone generate a token (usually a random string), store it in the backend and then send the copy back to the client
4. Every request from client will attach the token and keystone will verify the token(matched? Expired?)
5. If valid, keystone will return the 200 and process the request, otherwise will be an 401 then reject.
See workflow here:
UUID is quite simple to implement but since
every requirement will be via keystone and it could be the bottleneck in the
large scale cloud.
PKI token
PKI token was introduced since Grizzly.
The workflow is similar but the token is based on X509 PKI
while Keystone is the CA.
0. When keystone was installed , we need to generate the keys and certs including CA private key, CA certificates, Signing private key, Signing certificate.
1. When client provides valid username/password pair, Keystone will use Cryptographic Message Syntax (CMS) to produce CMS token out of the following data: Service catalog,User roles,Metadata
2. The token will be cached in keystone and send back to client.
3. When the requests come via API, they will attach the CMS token , the API has got keystone’s copy of Signing certificate, Revocation list, CA certificate so it can check the validity of token offline (without contacting keystone)
4. If valid, keystone will return the 200 and process the request, otherwise will be an 401 then reject.
0. When keystone was installed , we need to generate the keys and certs including CA private key, CA certificates, Signing private key, Signing certificate.
1. When client provides valid username/password pair, Keystone will use Cryptographic Message Syntax (CMS) to produce CMS token out of the following data: Service catalog,User roles,Metadata
2. The token will be cached in keystone and send back to client.
3. When the requests come via API, they will attach the CMS token , the API has got keystone’s copy of Signing certificate, Revocation list, CA certificate so it can check the validity of token offline (without contacting keystone)
4. If valid, keystone will return the 200 and process the request, otherwise will be an 401 then reject.
See workflow there
Further reading blog:
http://www.mirantis.com/blog/understanding-openstack-authentication-keystone-pki/


Hi,
ReplyDeleteKeystone is an OpenStack project that provides Identity, Token, Catalog and Policy services for use specifically by projects in the OpenStack family. It implements openstack’s identity api. Good job! Thanks for sharing. To know more information click here OpenStack Administration Online Training.